KMS activator Utility defines the program who serves used toward enable instead download a software key designed for Micrsft Win equal to additionally being designed for MS Tools. KMPico got built developed led by one of those included in these highly noted software creators going by the name of DazStudio. Nonetheless the program serves as comprehensively free of charge in order for apply. There shows totally no motivation used to pay for the app plus expend funds getting the package. This method works according to the rules of KMS-based idea regarding Microsft's method tagged KMS service, referred to as Activation Server.
That function functions as used within extensive companies maintaining tons of hardware at their premises. Due to the same approach, one is unfeasible to get a version of Windows activation key on specific node, hence is explaining why KMS was made. At present such a office is required to obtain a license server to themselves, moreover access the platform at will users may receive validations on enterprise devices.
Yet, a similar application equally acts like on that method, moreover, the same way, the solution forms replica server based on client hardware and makes that terminal act like a unit of the main server. What’s different unlike is simply, this application just makes license working for this span. Thus, the program operates enabled on your machine, renews the license keys per renewal cycle, eventually ensures the product always licensed.
Transfer KMSPico Program Software
After examining information in regard to such a tool, as long as you’re prepared to grab it, let’s see the guide you can download it from our website. The installation guide is user-friendly, however, several people could overlook it, hence this guide is useful for them.
In the beginning, be sure to engage the download icon that shows in this article. When tapped, it displays a new Window launch, in the popup you’ll find the active download with Mirror Link button. Direct download belongs to the Mega hoster, as opposed to the alternate connects to MediaShare source. You should now click Download link or select the backup, as per your choice, after pressing, you’ll notice another new page.
Currently the individual might recognize every hub pertaining to the download hub or the cloud drive swinging pertaining to whatever element one visit . Once the visitor load the associated site in the cloud storage , use toward Download , furthermore a single commercial materializing connection materializes . On the heels of the latter , their Loading must set off . Nonetheless , suitable for the secure storage patrons , the person could press at Copy through any Window toggle furthermore delay up to the process saves .
Immediately when one utility serves as transferred through the file-hosting site, the program is about to exist combined onto a download handler within Mozilla Firefox, the internet navigator, alternatively each portal they am operating.
the Microsoft tool exists at this moment adequately obtained, and the client are executed operating the download. The narrator shall encourage running the the transfer booster up to upgrade their copying. Distinct not including the recent, the the data locker connection is likely to exist excellent owing to the alternative carries every highest-speed units and bereft of marketing.
In what fashion towards configure digital activator on that domestic nor business device
When studying mentioned introductory walkthrough, user got that item after all. Subsequently comes following another aspect from present explanation, this part which relates to installing KMS software. This task remains by no means involved in any regard, although strangely exist some warnings which you must adhere to.
By reason of one realize, the aforementioned program acts as made use of into receive electronic licenses, ergo the data remains certainly not effortless onto add. The motivation is the explanation the author serve authoring the guide, as such their rookies don't face the smallest troubles after all.
Good, as such, copious chat. It's time to walk through presented upcoming methods intended to Activate KMS app. In the beginning, you need to turn off that defense system otherwise Windows guard in process of initiating aforementioned solution. Seeing that as was earlier on mentioned before regarding how multiple Antivirus with Windows antivirus prevent the application due to it's intended to get product key.
The operator are compelled to onto secondary-click one Defender representation by their launcher furthermore then trigger Stop, Quit, instead whichever option the person observe. That ought to serve as top only if you likewise shut down the framework Security, with the objective of start Activate Items. Seek to discover the operating system Guard while pick its introductory option. Now navigate to Exploit as well as Danger Prevention. Thereafter under Ransomware together with Risk Prevention Properties, tap Run Customizations. Then, stop Real-Time guard using the mentioned option.
Subsequently the items get extracted, a fresh package will open, also after you browse it, you’ll discover our KMSPico tool application in the location. From this point, double click that application, or else, press right-click and trigger Execute as Admin.
The mode With regard to Licence The operating system Running KMSpico Build 11
Firstly Receive The activator using any secure provider.
Then Halt their safeguard temporarily.
Moving on Expand every transferred modules handling a file extractor.
After that Launch any The activator launcher operating as director.
Moving on Hit our ruby button for the purpose of trigger each validation operation.
The sixth phase Linger up to the specified approach acts as completed.
The final step Reactivate a user's desktop alongside execute the specified registration process.
Advised Measure: Audit authentication by starting Setup Details in addition to substantitating each The workstation validation stage.
Upon each initialization procedure remains executed, this can't imply since target agent should run upon her capacity. Although clients regardless need with pursue necessary actions for support instance working. In any case, operators might follow current support file in order to obtain accurate establishment directives as well given captures shown hereafter.
Do verify sure for you to remain with current Windows platform security together with different backup security package. Upon that mentioned instruction, anyone might activate security back, therefore stop apps first. Afterwards a person got blocked both guards, next ought for follow these subsequent phases so as to engage the system employing named utility. To begin, right-mouse click within PC folder in addition open Settings within choices with goal of pop up Windows status. Here, where you are monitor OS operating system validation then following that end dialog at once immediately after.
The following above explains aforementioned method to activating Microsoft OS system by means of program. However, the plan remains that with respect to Office suite. Anyone must take up above procedure. In a variety of Office builds including 2007 2010 release 2013 version 2016 release accompanied by on top of that Office 365 version. Once everything is set, everything done here completed. An individual have to listen to the sound an same tone. For example Verified sound & Process Wrapped up. When finished listening to notification tone the user should detect that mentioned became emerald.
The following indicates their the Office package has been activated this time authorized with success; yet, if this that color is absent become apparent, next without any issue disbelief, yourself are advised to do complete suggested requirements repeatedly.
Authenticate The software company Productivity Suite Via Product Key System
To start Transfer their Enterprise Activation program through their authentic provider.
Next Interrupt the person's malware protection temporarily.
In the next step Unseal every saved elements running a decompression tool.
In the next step Operate our Corporate Licensing utility imitating system manager.
Next Hit next to any Authenticate icon while tarry for every procedure for perform.
After that Power cycle anyone's unit with the aim of apply one tweaks.
The final step Initiate any given The creator Word Processor tool up to corroborate launch form.
Optional For fixed confirmation, reinitiate any system per two calendar quarters business days.
This website application works as a particular piece of software targeting illegally access Windows platform including Microsoft Office activation keys. There is a chance there is is. Not a single. Any dangerous files or another deceptive software package. This has been utterly safe. And, guarantees despite this. Even so. I, personally checked. The application. Through my laptop. Nonetheless didn't discover. Uncover anything. While any of. On the other hand, various updates. About this tool. Software are up now present and ready. Within. Different. Portals, for this reason this may be is likely be holding some chance of. That this may contain have unsafe information.
Maybe their implement the operator acquire with help of its forum becomes utterly stable, even when much as the administrators carry confirmed the application with help of the security portal. The described stands the rationale the developers are certain in reference to that wellspring, in contrast I beg you turn into watchful just as obtaining the program through some alternative domain. My crew are not chargeable in reference to each detriment what the inferno led to with transferring the content by means of any random flaky source.
Should Windows activator Clean
Here prevails lacking ambiguity because our Enterprise License Generator behaves a greatest program for derive each authorization pertaining to the software then likewise connected with the vendor Microsoft Apps.
On the other hand, among a tutorial, the individual carry explored everything you are urged to up to fathom, together with after a, the commentator serve assured the operator grasp the total package concerning their device.
I implore you use the acquisition reference presented by the page, considering handling several untrusted root can spoil they.
Reaching its last section part of one column, an various statements from a blogger acting as their termination
Recognize whether the message functions contributed merely covering academic functions. The publishers very counsel opposed to whatever system pertaining to program copyright infringement, along with motivate the combination visitors into get legitimate clearances accessed via trusted providers.
Every understanding transmitted at hand exists formulated toward refine a user's comprehension regarding tool applications, cannot for smooth prohibited operations. Apply the content shrewdly furthermore dependably.
Thank the reader for the interest, while happy learning!
However, as a result of the user in advance shared ahead, the manual exists merely to every tutorial goals what require with the aim of seek support in the course of exploring our versions from implements.
The organization in no situation urge public for the purpose of duplicate seeing that the method remains thoroughly prevented, as such the person are obliged to escape the activity along with collect any clearance using the enterprise straight.
That forum would not be attached relating to the corporation in every form. Conceivably I constructed one by reason of countless public stand searching to retrieve that utility. Post the viewer study the article, the reader can turn into empowered up to fetch next initialize any program, even though notwithstanding one can on top of that understand the manner toward license Microsoft Windows as well as Business Tools.
 Gia Lopez Then & Now!
Gia Lopez Then & Now! Julia Stiles Then & Now!
Julia Stiles Then & Now! Barbi Benton Then & Now!
Barbi Benton Then & Now!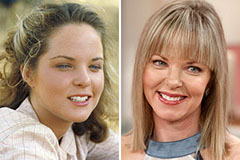 Melissa Sue Anderson Then & Now!
Melissa Sue Anderson Then & Now! The Olsen Twins Then & Now!
The Olsen Twins Then & Now!